Valve Anti-Cheat Untrusted Bans (VAC) CSGO
So recently I’ve seen people surprized at how they are getting ‘untrusted bans’ on cheating forums. Some even confused at what that term even means.
Even though Valve hasn’t given us a definition of what it means previously it was understood that an ‘untrusted ban’ was the serversided anticheat ban given to players who send incorrect data to the game server in Valve’s official matchmaking. Most prominently player view angles which are stored in the Euler format (X,Y,Z) (Pitch, Yaw, Roll) if sent incorrectly to the game server instantly will flag your account as ‘untrusted’.
Heres some MSPaint diagram I drew showing you what I mean by invalid viewangles and how this is a big no no when the server receives them.

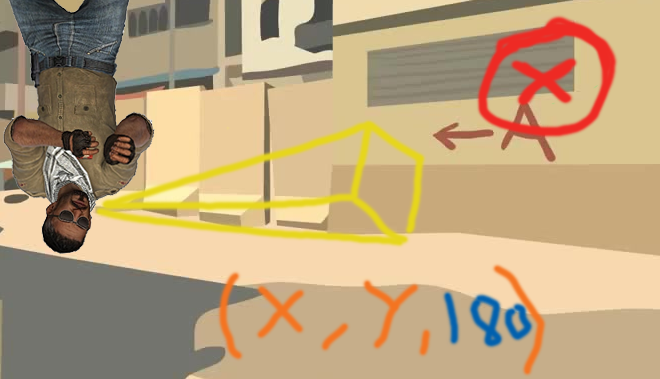
Now without going way off topic let me just point out whats going on, obviously the game character can not be upside down in CSGO there is no possible way for this to happen therefore if the Valve Offical Matchmaking Server receives 180 for the roll angle for example in this case they will instantly flag your account for a ban.
Untrusted bans however have evolved from that, people are getting untrusted bans with correct viewangles and you see the same sort of replies people make on forums online. “You forgot to clamp your angles properly”, “You must of wrote wrong viewangles” when in fact it could be something else causing these types of bans.
Now disclaimer I present to you my take on things this isn’t necessarily why it happens but I believe strongly it’s very likely to be the case based on research I’ve done on the Valve Anti-cheat system.
LoadLibrary
When you load an internal hack into a game (in this case csgo) usually the easiest way to do so is to call a function exported by KERNEL32 called LoadLibrary. LoadLibrary comes in many variants and since it’s the easiest to use one can quickly whip up an injector for their hack or copy paste one from the Internet and make it work.
Now lets talk about VAC3, one of the process scanning modules that resides in VAC returns all loaded modules in CSGO (or the target process) at the time of the scan.
It returns:
- ModuleBase
- MD5 Hash
- VolumeSerialNumber (the module is stored on)
- Some other attributes also present in structure
BY\_HANDLE\_FILE\_INFORMATION
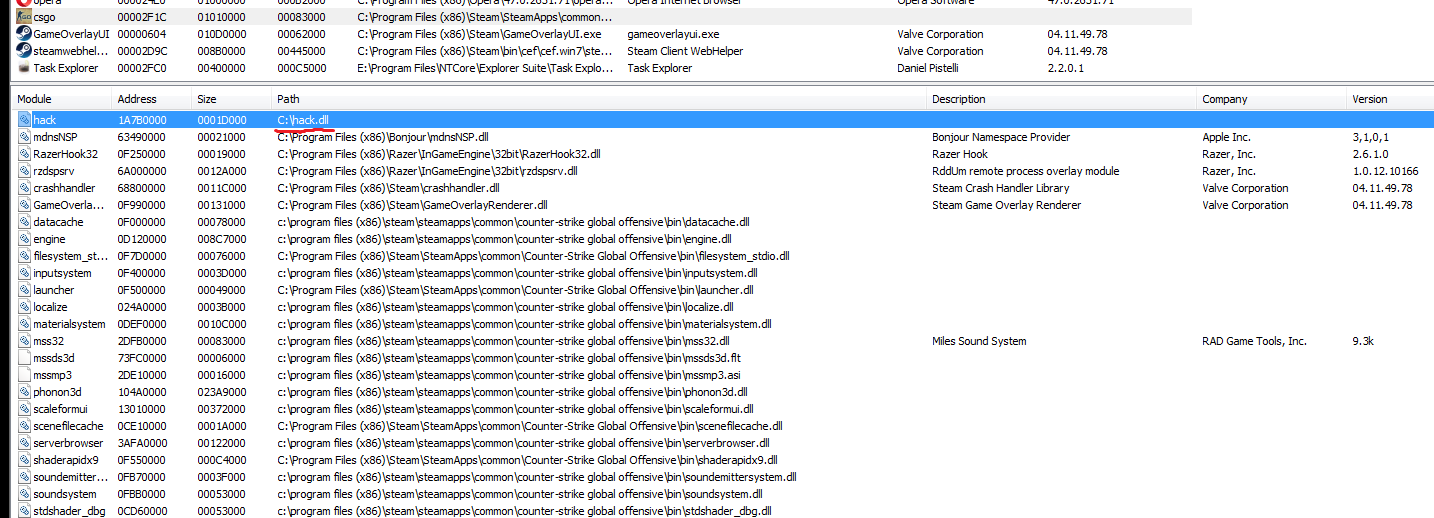
It also has the ability to do deeper scans on individual modules, one of the more interesting scan flags returned is the fact if the module mapped in memory is present in the module list (PEB). Some people using LoadLibrary think it’s smart to unlink their hack module from the PEB which makes it appear even more suspicious as they can easily tell and do log this when scans are run.
(Here is a zip file containing said module and a IDA idb file which has fixed imports and decoded strings)
Scan Function is @ 0x10002f07
So where am I going with this you may be wondering? Well 2017.05.02 there was a CSGO update which bought some sneaky changes to game integrity.
http://blog.counter-strike.net/index.php/2017/05/18665/
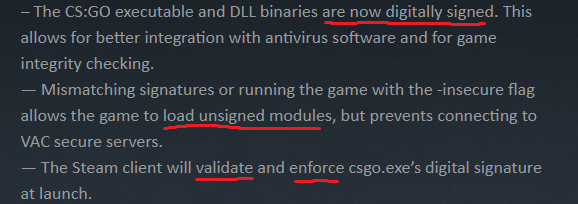
At first it appeared they did this to stop anti-virus vendors from incorrectly flagging CSGO’s DLL libraries as malware (false positives). However if you think about this was a pretty strategic move on Valve’s part to help them isolate potential cheat specific DLLs.
Since VAC is constantly collecting data from you and I they have a massive sample size of loaded DLLs that could be present in CSGO besides their own signed modules which you can not alter. For example they can easily rule out their official DLL libraries from foreign ones.
There are a ton of legitmate applications which load libraries into other windows applications such as teamviewer ‘tv_w32.dll’ however Valve eventually collects enough data to determine that your hack dll you load everytime CSGO runs is in fact be a cheat and will deem your client as ‘untrusted’
Conclusion?
Write your own manual mapper, and don’t copy paste assembly stubs (they are signatured)
