VAC Banwave (13/09/2016)
A few days ago there was a massive VAC ban wave. Some of the major P2C providers got hit:
- Interwebz
- UnityHacks
- Aimware
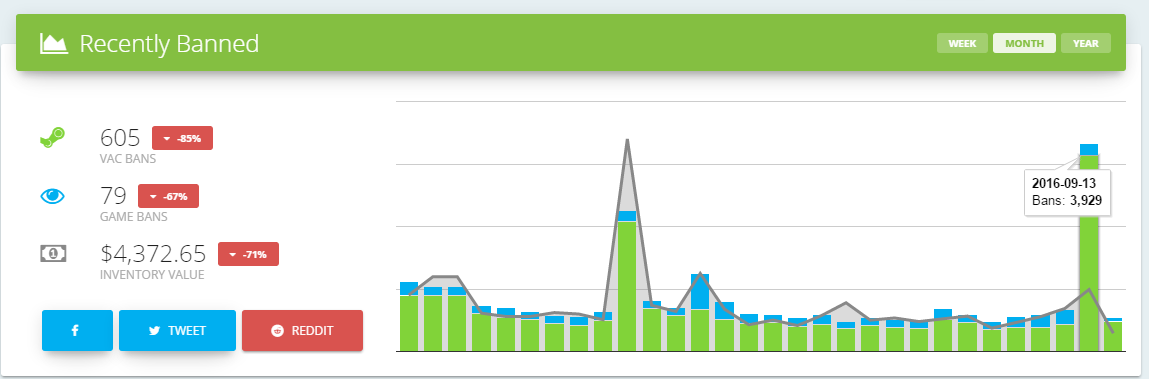
Other providers got hit but I’m not aware of who they are. News sites are reporting this to be the largest ban wave of the year. Firstly I’m going to start by saying this is not a server side detection as a big post on reddit and various other sites have threads titled “untrusted ban wave”. Untrusted though yes mostly is a ban that occurs when the server side anti-cheat detects an anomaly or something that shouldn’t be set on your client however it can also occur when the clientside VAC scanner detects an injection occurring. These bans are delayed as far as I know as when I was using the public Xenos injector I received an untrusted ban which later showed up on my profile as a VAC ban.
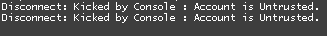
So moving on.. This ban wave was in fact a normal VAC ban wave.
File: vac_module_0_ee76faea4b2d4cdb951ebd9dcff92799.dll
Size: 61KB
Export TimeStamp: 13/09/2016 4:27:31 AM
Debug TimeStamp: 13/09/2016 4:27:31 AM
.text hash: F0B95B4B38F1752FDFCD7E7F6779165339E93FB2
File: vac_module_1_3d7b7d8d50356e415bebe04ad1464257.dll
Size: 60KB
Export TimeStamp: 3/09/2016 6:16:46 AM
Debug TimeStamp: 3/09/2016 6:16:46 AM
.text hash: E922440FEF9D16FCD1DD55329B2C43D2F0EBF7F8
The morning I woke up to the ban news I did another VAC module dump and clearly you can see they updated their modules. The 60kb module is responsible for scanning processes. The 61kb is an updated version which fixes an issue for windows10 (how02 found this). My guess is this VAC wave was targeting P2C loaders and processes that spawn before injection into the game. Remember VAC now can start when you login to Steam so running a potentially flagged loader even before the game is launched can see you VAC banned if you join a VAC secured server.
Lets see what the next wave brings us 🙂
